How To Protect Yourself From Online Identity Theft
Just not so long ago, when we thought of identity theft, we visualized a thief stealing personal information through dumpster diving, shoulder surfing or pickpocketing. But that's no longer the case.

Aura | Best Identity Theft Protection
All-in-one, easy-to-use identity protection for you and your loved ones.
- 3 Bureau credit monitoring
- Identity Protection
- Password Manager
- Antivirus
- VPN
- Credit lock
- Family identity protection
- Dark web monitoring
In the cyber-focused 21st century, identity theft prevails online. Online identity theft usually takes place when your personal data is leaked through hacking, phishing, data breaches, social media oversharing, and other means.
With a stolen identity, the imposter can then do a wide range of illegal things(taking over existing accounts, opening new credit lines, getting medical treatment, committing crimes, etc.), stripping their victims out of money, reputation, and peace of mind.
Identity theft is real. And although there isn’t an ironclad solution, there are 7 actionable steps you can take to protect yourself from online identity theft. Read on…
1. Protect your personal information online

Your personally identifiable information (PII) – such as your name, phone number, home address, photos, social security number, and banking credentials – can be easily traced to your identity and exploited for identity fraud. So first and foremost, keep your personal information personal and limit what you share online, particularly on social media.
Also, keep your guard up for phishing. Malicious actors may pose as a legitimate company or representative to lure you into revealing your personal information. Phishing comes in a variety of forms. It could be a suspicious phone call, an urgent email, a well-crafted text message, or a too-good-to-be-true deal in the disguise of a legitimate-looking website – but think twice before you act. As a general rule of thumb, always verify the source before giving out your personal information.
2. Practice good password habits

A lot of people use simple or easily guessable passwords because they’re easy to remember. But that also makes your personal information a low-hanging fruit to cyber criminals. According to the Verizon Data Breach report, 81% of hacking-related breaches involve a weak or compromised password. So to protect your online account security, there are some good password habits to get into and some bad ones you should avoid:
- Avoid using obvious information like 123456789, 555555, qwerty, etc.
- Avoid using information related to your identity, such as your name, zip code, birthday, the last four digits of your social security number, etc.
- Make sure your password is long, complex, and unique. The FTC recommends creating a password that is at least 15-character long, with a healthy mix of case-sensitive letters, numbers, and symbols.
Need help creating a strong password? Use our Super Easy Password Generator. - Enable two-factor authentication (2FA) on devices and accounts. 2FA requires you a second step after providing a password, which adds an extra layer of security to your account in case your password is stolen.
- Make sure all your devices are password-protected.
- Avoid using the same password across different devices or accounts.
- Update your passwords periodically.
Use a password manager
Good password habits are the foundation of your digital security, but they can be hard to maintain. If you don’t like the heavy lifting, consider using Lastpass. Lastpass helps you generate hack-proof passwords and provide real-time monitoring for your accounts.
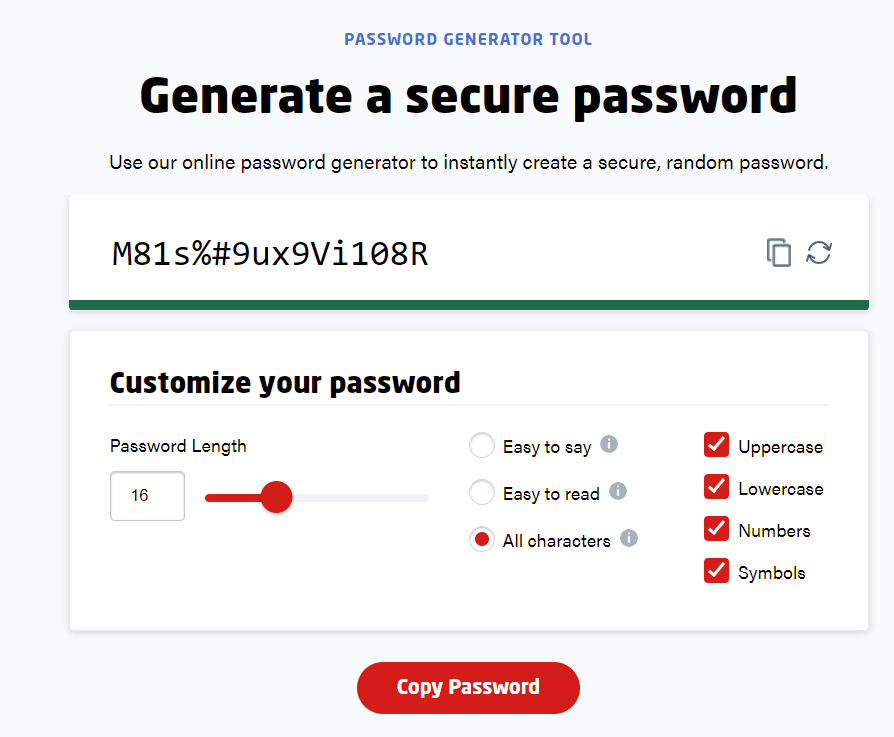
Or, if you want something beyond password protection, you can choose Aura, an 8-in-1 identity protection service that gives you 24/7 online safety and identity protection.
3. Install antivirus software

Outdated software and system may have underlying security flaws, making them vulnerable to cyberattacks and data breaches. To lower your risk of online identity theft, you should keep your system up-to-date. Installing an antivirus program may help. A good antivirus would detect malware, keyloggers, and phishing websites and protect you from ever-evolving online threats.
4: Be wary of public WiFi

We can’t reiterate this enough – public WiFi isn’t secure. There are a plethora of security loopholes with public WiFi networks. Perhaps the biggest problem is the lack of sufficient encryption (if any), which makes it a hidden goldmine for hackers and cyber snoopers to intercept personal sensitive data and utilize at their pleasure.
Another common tactic hackers may employ is a WiFi honey pot, also known as Evil Twin Attack, where a fake WiFi hotspot masquerades as a legitimate one (e.g. Free_Starbucks_WiFi, CityMuseumWiFi), only to trick you into connecting so that they can harvest critical details.
To secure yourself against WiFi hackers, our word of advice would be to avoid connecting to public WiFi. But if you must do it, DO NOT log into websites that require your login credentials, such as your email, social media accounts, or shopping websites.
Another way to keep you safe while using public WiFi is to use a VPN (Virtual Private Network). A VPN is a service that creates a secure and encrypted tunnel between your device and the server. There is practically no way someone can track your online activity.
5. Review your credit report

A credit report provides a summary of your credit history, which may include the number of new credit accounts opened in your name, payment history, debt owed, and other types of information. Since lenders and businesses use it to measure your creditworthiness, it is important that you review your credit reports regularly to detect identity theft at an early stage
To do so, request a free copy of your credit report. You can do it by calling 1-877-322-8228, or ordering it online at www.Annualcreditreport.com.
Once you get access to the report, have a thorough review and check for unauthorized activity. Any new accounts you don’t remember opening, transactions you don’t recognize or unexplained withdrawals may tip you off to identity theft in track.
Alternatively, you can consider using a credit monitoring service, which constantly monitors your report and alerts you when there are changes.
6. Monitor your statements

In the same vein, it’s important to regularly check your financial and medical statements. Track what bills you owe and be alert to suspicious activity – unfamiliar charges, withdrawals, medical care, and so on. Even a small amount should raise an alarm. Sometimes it could be the ID thief trying to test if you are aware, and if left unattended, it could signal to the thieves that the account is vulnerable and could be exploited for larger purchases in the future.
In addition, know when the bills are due. If you are not getting bills on time, call the company to investigate. It could be a clue that someone steals your identity and changes your contact information.
Read more: How To Protect SSN From Identity Theft
7. Use an identity protection service

With ID thieves and cybercriminals continuously evolving their attacking tactics, protecting yourself from identity theft would feel like a never-ending chore. The six methods we’ve shared with you above are crucial in keeping your digital identity safe, but there is so much more to it. If you don’t have a DIY mentality, you can consider Aura, an all-in-one identity theft protection service to give you 24/7 protection against identity theft and fraud.
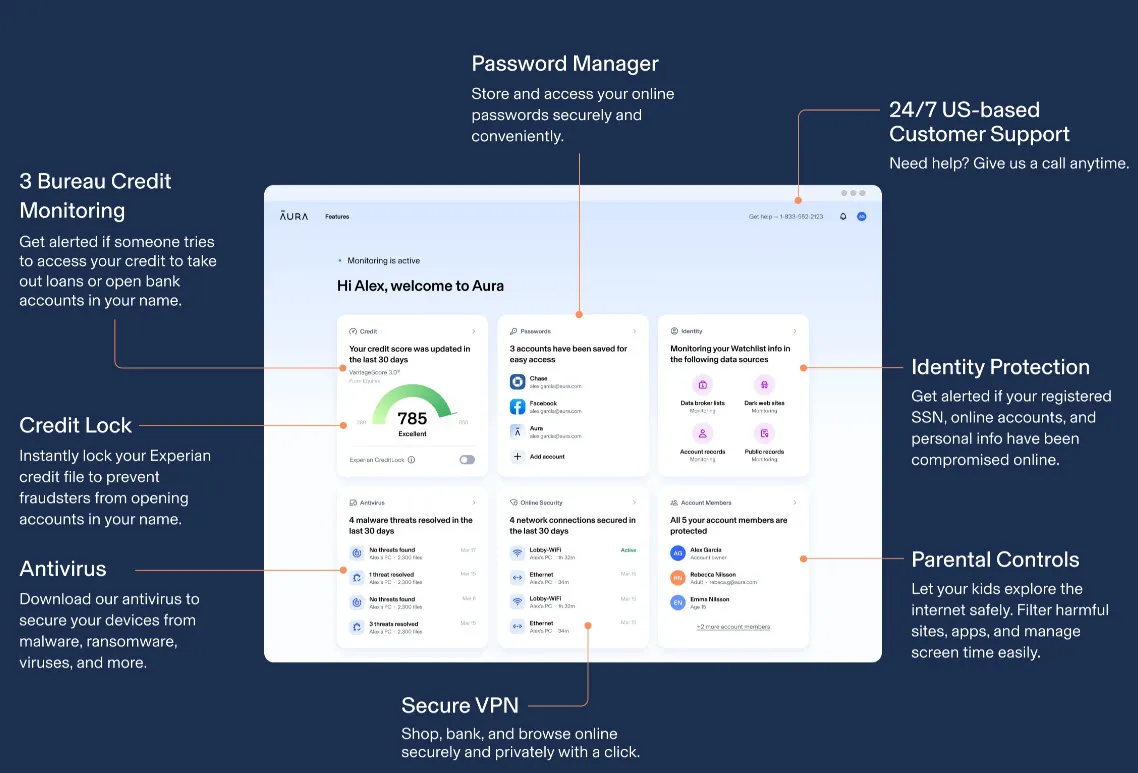
With Aura, you get:
- Credit monitoring – Suspecting someone would open new accounts or apply for loans in your name? Don’t worry – Aura will be on your side. It tracks your credit reports at the 3 major bureaus and notifies you if suspicious activity occurs.
- Identity theft and online account protection – Aura monitors your online accounts, PII, SSNs, and other types of sensitive information.
- Password Manager – Weak passwords may invite ID thieves to gain access to your accounts. To combat this, Aura makes sure to create strong passwords and secure them.
- Antivirus – Aura’s antivirus software gives you 24/7 protection from malware, ransomware, virus, and more.
- VPN – With Aura’s military-grade VPN, it’s only one step away to shop, browse, and bank securely and privately.
- Credit lock – You’re free to lock your Experian credit file to prevent your credit from being exploited.
- Family identity protection – Protect your family from financial fraud, theft, and other types of online threats.
- A $1,000,000 insurance policy – You’ll be covered with up to $1 million for loss incurred as a result of identity theft.
Run a dark web scan with Aura
How much do you think someone has to pay in order to access your credit card information? The answer is as little as $5 on the dark web – it may surprise you, but the dark web is where most criminals buy and sell information, and it can be dirt cheap.
Here is how to run a dark web scan to find out if your personal info is leaked on the dark web or in other places where it shouldn’t be:
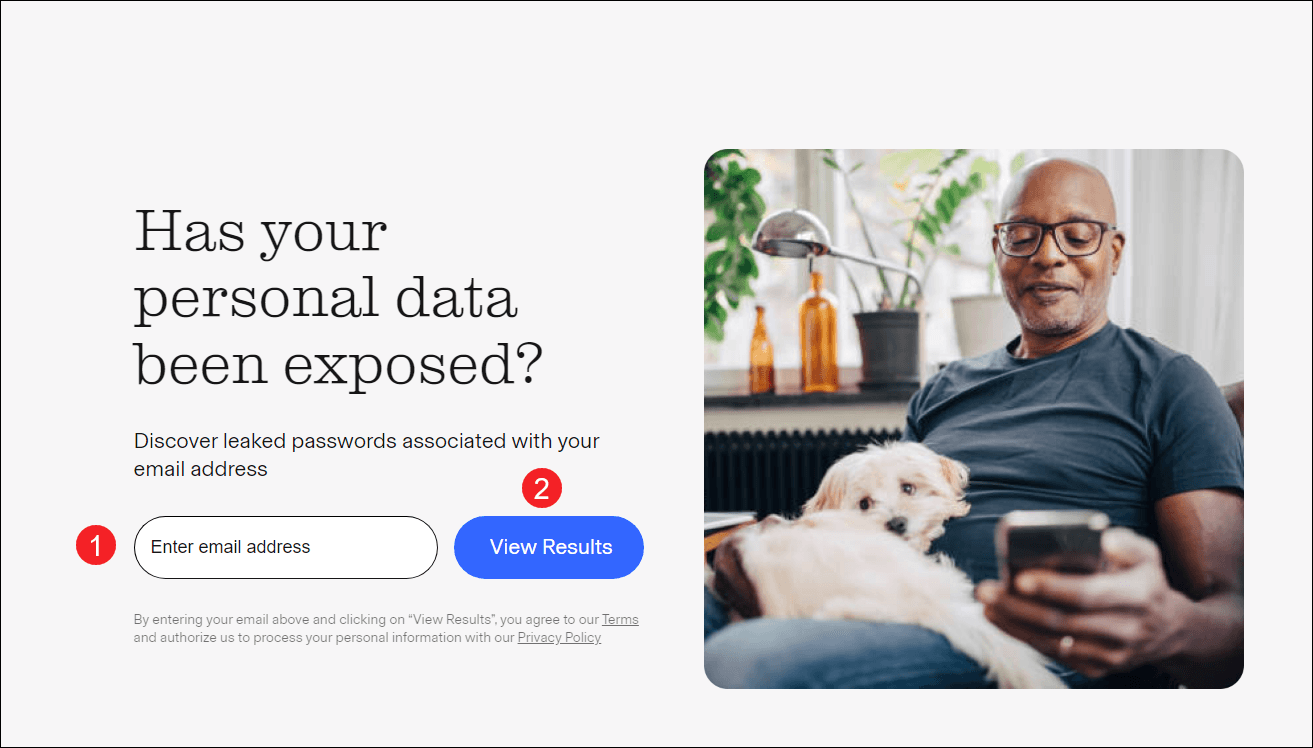
- Go to the Aura Free Scan page.
- Enter your email address and click View Results.
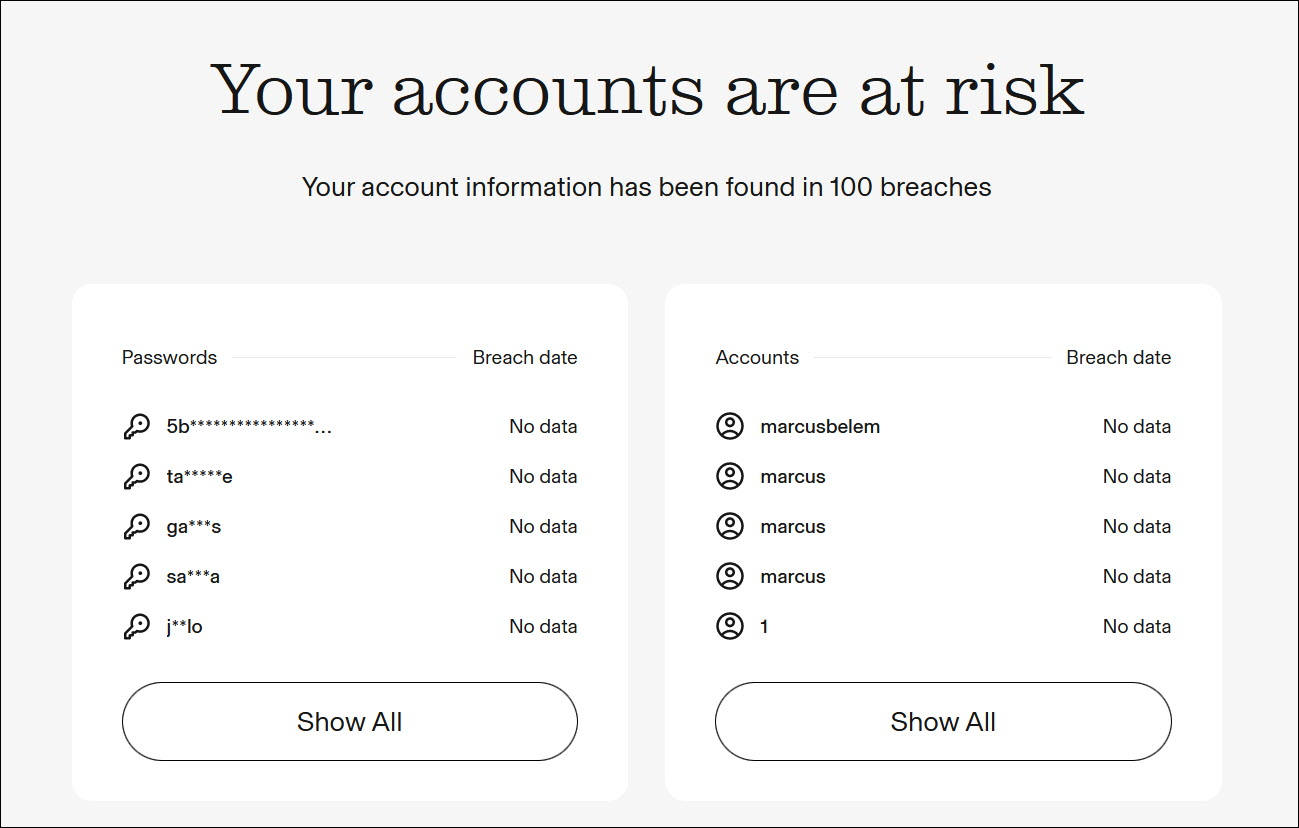
- Aura will check if the information associated with your email address is being exposed in data breaches or ends up on the dark web.
- You can start the 14-day free trial to access the full report, along with its full suite of identity protection tools.
Summary
As our reliance on the internet grows, so too does our vulnerability to cyber threats. Today, it doesn’t take a bad actor to snatch your wallet or poke around to access your personal information. More often than not, identity thieves steal your personal data through public information, phishing, scams, or data breaches. Luckily, in this article, we’ve put together 7 proactive methods you can use to prevent online identity theft. Hopefully, it has helped.
If you have any ideas, questions, or suggestions, you’re more than welcome to leave us a comment below.
Image credits:
Image by Freepik
Image by rawpixel.com on Freepik
Image by Drazen Zigic on Freepik
Photo by Dylan Gillis on Unsplash
Photo by Bernard Hermant on Unsplash
Photo by rupixen.com on Unsplash



 View all of Enya Zhang's posts.
View all of Enya Zhang's posts.
![[SOLVED] How to protect your online identity [SOLVED] How to protect your online identity](https://www.supereasy.com/wp-content/uploads/2022/11/online-identity-protection.jpeg)
![Sorry There Was a Problem with your Request Instagram [FIXED] Sorry There Was a Problem with your Request Instagram [FIXED]](https://www.supereasy.com/wp-content/uploads/2018/10/request.jpg)